What is a Network Loop? What is the harm of Network Loop? How does the Network Loop happen? How to avoid?
1. What is a network loop?
Network loops are divided into layer 2 loops and layer 3 loops. All loops are formed due to confusion caused by unclear destination paths. For example, in layer 2, when a broadcast message passes through two switches, it will Broadcasts are continuously generated in a vicious cycle, resulting in loops. In the third-layer loop, the original router unexpectedly fails to work, causing route advertisement errors, forming a vicious circle. In actual application environments, the occurrence of second-layer loops is relatively rare. common.To put it simply: when two switches are connected, they should be connected with one line to achieve the cascading effect. If two lines are used to connect, a loop is formed. In addition, if multiple switches are interconnected, a loop can also be formed, especially if they are different. Regional, very difficult to find.
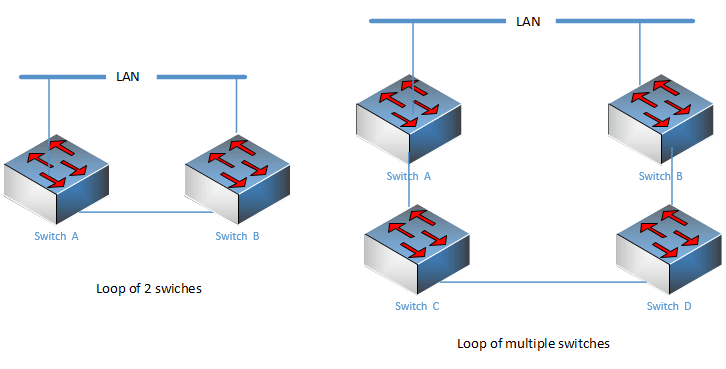
2. The harm of network loops
There are three main dangers of network loops:
—Broadcast storms
—Multiple Frame Copies multiple duplicate data frames
—MAC Database Instability MAC address table is unstable
1) Broadcast storm
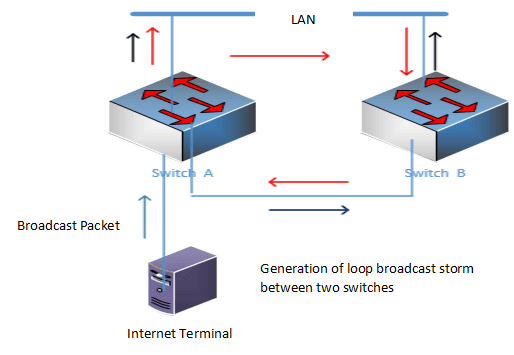
When a data frame or packet is transmitted to each node on the local network segment (defined by the broadcast domain), it is a broadcast; due to network topology design and connection problems, or other reasons, broadcast packets are copied and spread in large numbers within the network segment, resulting in Network performance is degraded, or even the network is paralyzed. This is a broadcast storm.
The root cause of the broadcast storm is that the data frame forms a loop, and there is no TTL structure in the frame header, so the frame is always valid. Since the broadcast packet does not have a specific destination address, it will be forwarded forever in the network.
2) Multiple repeating data frames
In the figure above, if the terminal wants to send a data frame to the LAN, it will be found that there are two paths, one is through switch A to the LAN, and the other is from A to B and then to the LAN. In this way, there are two paths in the LAN. the same data frame.
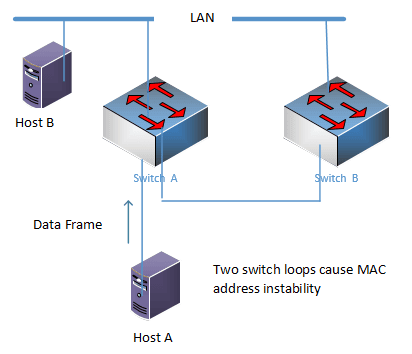
3) The MAC address table is unstable
Host A sends a data frame to host B. B’s MAC address table has not been learned by the switch. The data frame is sent to switch A and switch B along the link. Then switch A and switch B both record the MAC address of host A in the lower link. port. Because the data frame is received through the downlink port, it will be flooded out through the uplink ports of the two switches and cross to the uplink port of the mutual switch. The port corresponding to the MAC address of host A is considered to be the uplink port. port, that is, the data frame sent from switch A arrives at the uplink port of switch B. Then switch B receives it and floods it again through the downlink port, and so on. The data frame repeats the above process in the loop. Switch A and switch B uplink repeatedly learn from host A on the uplink port and downlink port. MAC address, causing instability in the MAC address table.
3. Phenomenon when a network forms a loop
When a network loop occurs, network performance decreases, network latency increases, intermittent interruptions occur, packet loss is severe, and services cannot be operated until the network is completely interrupted.
How to avoid network loops
Network loops affect network communication quality. To avoid network loops, you can implement the following strategies.
How to avoid network loops
Network loops affect network communication quality. To avoid network loops, you can implement the following strategies:
How to avoid network loops
Network loops affect network communication quality. To avoid network loops, you can implement the following strategies:
Avoid inappropriate physical connections
Physical connections are the basis for establishing a network. Improper physical connections will produce routing loops. Therefore, physical connections should be strictly controlled and cabling schemes should be optimized to avoid unnecessary connectivity.
Use network loop avoidance protocol (STP)
STP is a protocol used to eliminate network loops by establishing a tree topology to avoid large amounts of data transmission between nodes. Using STP can effectively reduce network loops and ensure the quality of network communication.
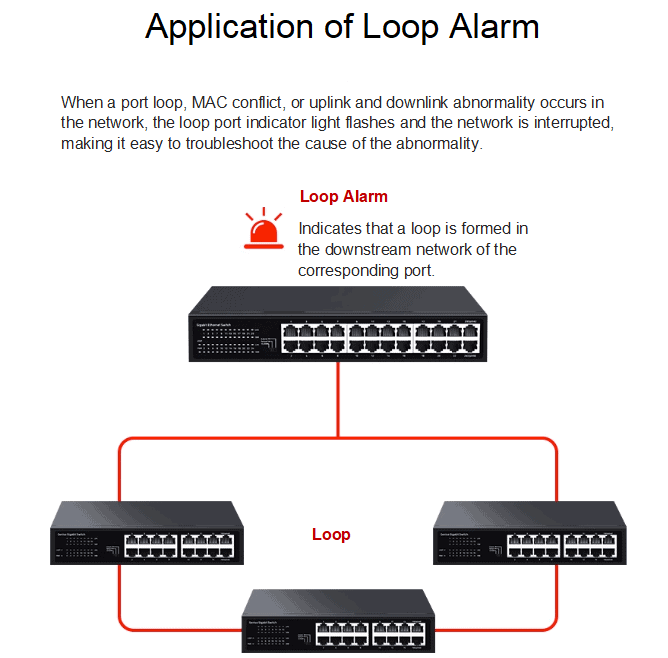
Use switch supporting Loop Alarm / Loop Detection and Prevention. There are gigabit unmanaged Ethernet switches support Loop Alarm, Web-managed switches support Auto Loop Detection and Prevention, L2 L3 managed switches support STP and futher protocol.